Hacker groups going after government domains
Hacker groups going after government domains Security researchers are suspecting state-sponsored actors. Imagine typing in a government internet address, and ending up on a website that looks like a government website, acts like a government website, but steals your...
City licensing cybersecurity software modeled after human immune system
The city of San Antonio is licensing software to enable its cybersecurity team to secure its internal computer network. The City Council on April 18 approved a 5-year contract of $670,620 contract that runs through 2024 with a local Austin-based technology...
Hackers broke into university networks in just 2 hours
Hackers broke into university networks in just two hours Penetration testers testing university networks were able to use phishing emails to gain administrator access and access personal data, financial information and confidential research. Ethical hackers testing...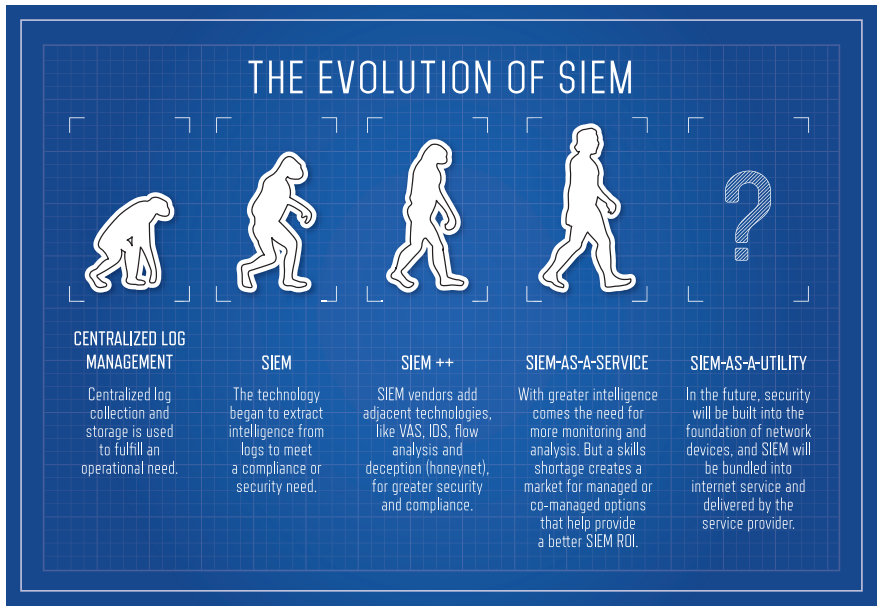
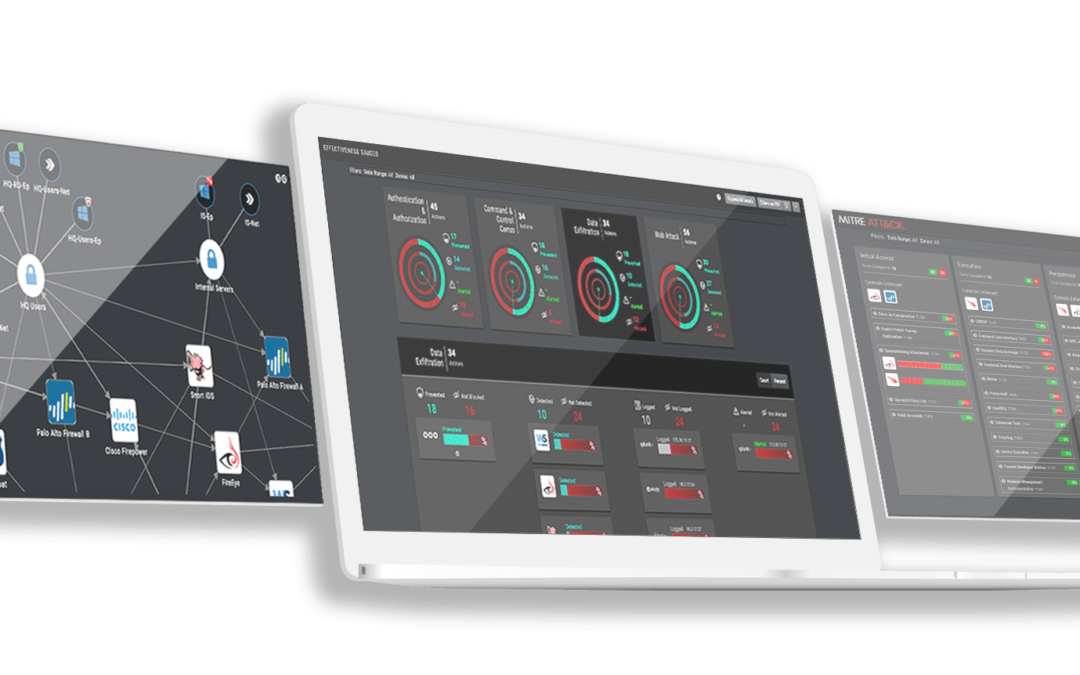
Best-in-class SIEMs and Honorable Mentions
Security Information and Event Management (SIEM) is a key enterprise security technology, with the ability to tie systems together for a comprehensive view of IT security. While each vendor has its own take on SIEM, Gartner lists the primary features for...