Who has time to read the the countless product fliers, brochures, or watches vendor webinars. But I do make time to read the Cherub cyber-blogs. They are following (and most of the time are ahead of) the industry trends in cybersecurity and data protection while boiling it all down to easy reading.
CASB, Castles in the Air, and why Surprises Lurk within Your Cloud Data Security
CASB — cloud access security broker — it’s the fastest growing security category ever — or so Gartner has claimed. And in the age of the cloud, in the age of data, security takes on a new level of importance but also complexity. Take the castle There was a time when...
Hacker groups going after government domains
Hacker groups going after government domains Security researchers are suspecting state-sponsored actors. Imagine typing in a government internet address, and ending up on a website that looks like a government website, acts like a government website, but steals your...
City licensing cybersecurity software modeled after human immune system
The city of San Antonio is licensing software to enable its cybersecurity team to secure its internal computer network. The City Council on April 18 approved a 5-year contract of $670,620 contract that runs through 2024 with a local Austin-based technology...
Retiring legacy DR for DRaaS benefits can be well worth it
Retiring legacy DR for DRaaS benefits can be well worth it The benefits of disaster recovery as a service include lower cost, enhanced reliability and streamlined administration. It's no wonder that more organizations are being drawn to it. "Disaster...
Hackers broke into university networks in just 2 hours
Hackers broke into university networks in just two hours Penetration testers testing university networks were able to use phishing emails to gain administrator access and access personal data, financial information and confidential research. Ethical hackers testing...
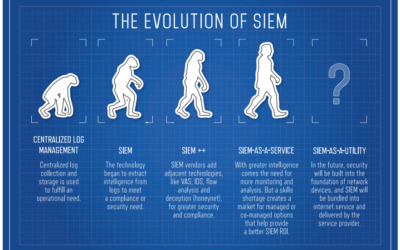
Best-in-class SIEMs and Honorable Mentions
Security Information and Event Management (SIEM) is a key enterprise security technology, with the ability to tie systems together for a comprehensive view of IT security. While each vendor has its own take on SIEM, Gartner lists the primary features for...
DON’T GIVE UP ON YOUR SIEM!
DON'T GIVE UP ON YOUR SIEM! It's hard to get SIEMs to work right, and even harder to keep them working. OVERVIEW SIEMs are a significant investment for security programs and they can provide huge value. However, as we all know, it’s challenging to properly...
The Urgent Need for Security Instrumentation
"The convergence of business and security is why I think Security Instrumentation is so exciting." Report: The Urgent Need for Security Instrumentation Detroit-based cybersecurity research analyst and bestselling author Richard Stiennon describes...
2018 Cost of a Data Breach Study by Ponemon
2018 Cost of a Data Breach Study by PonemonCherub is proud to sponsor the 13th annual Cost of a Data Breach study, the industry’s gold-standard benchmark research, independently conducted by Ponemon Institute. This year’s study reports the global average cost of a...