Validate Cybersecurity Effectiveness
REPORT:
SECURITY EFFECTIVENESS
The goal of this report is to highlight the trends and
common problems that Verodin SIP is consistently uncovering.

CONTROLS EFFECTIVENESS
OPTIMIZE & RATIONALIZE
ENVIRONMENTAL DRIFT DETECTION
UNDERSTANDING RISK
REMOVE ASSUMPTIONS.
PROVE SECURITY.
Practitioners know that you can’t just “set and forget” security products. There is a massive disconnect between out-of-the-box configurations versus potential capability. Every environment is unique, and, if not properly calibrated, organizations can miss out on significant value from security technologies. To add to the complexity, environments are constantly shifting, so there is no guarantee that a control that is working today will remain functional tomorrow. Verodin tightly integrates into the defensive stack and empowers security teams to continuously challenge and verify that every control is functioning as intended.
Verodin’s Security Instrumentation Platform (SIP) combines test execution with defensive stack integration to produce reports that demonstrate the effectiveness of deployed network, endpoint, email, and cloud controls. SIP’s dashboards and reports enable the user to identify high-level areas of weakness and strength, as well as targets for optimization. By removing assumptions and actually testing and challenging controls, organizations can prove which controls are adding value, which can be optimized and which can be removed from the stack.
Product Showcase for Security Instrumentation
Optimize & Rationalize
For example, drilling down from an understanding of how they are defending against malware delivery into the details of each test and then down to the specific threat and signature IDs within their controls that need to be configured to block.
The Pathway to Understanding Cyber Risk
- Remove Assumptions and validate control effectiveness
- Optimize the controls you have already purchased and deployed
- Understand the real gaps and target them with evidence-based tests
- Rationalize cybersecurity spend by removing overlapping controls
- Combat environmental drift by continuously validating effectiveness
- Continuously test the production IT environment against the threats and scenarios targeting business critical assets
- Drive decision-making based on the resulting data-driven metrics
Advanced Environmental Drift (AEDA)
Control Effectiveness
Schedule you 30 minutes Deep Dive into “Security Instrumentation”
Customer Stories
IT’S TIME TO ALIGN WITH THE BUSINESS
CYBERSECURITY MUST BE MANAGED WITH MEANINGFUL METRICS
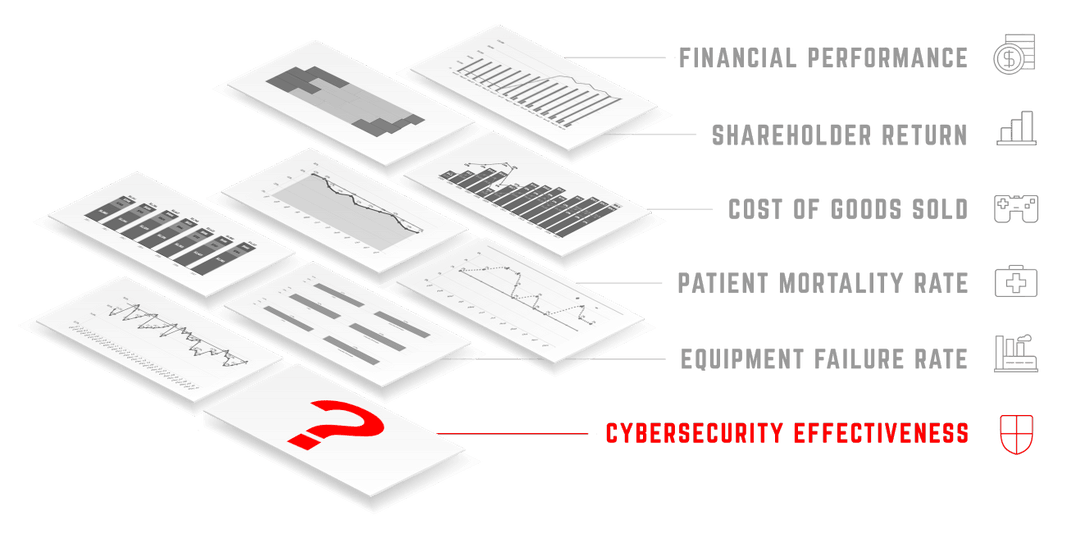
Executives rely on evidence to drive decision-making, optimize operations and ultimately improve their organizations over time.
Common assumptions:
- Technologies work as vendors claim
- Products are correctly deployed and configured (and stay that way)
- People are correctly handling events, and processes are effective
- Changes to the environment are fully understood, clearly communicated and correctly implemented
OUR PARTNER

Contact One of Our Security Instrumentation Experts





